Our team, ‘Bits & Pieces’, had a blast participating in the VSCTF event, and we placed 44th rank this time, It was a great run and we tackled some really interesting challenges! Here’s my writeup on the challs i solved in the CTF.
Reverse:
intro-reversing
Flag will be printed out straight away when you run the binary.
File: chall
We are given an elf 64-bit file, and as you know it’s a rev chall. Boot up that disassembler! On opening the file in binary ninja.
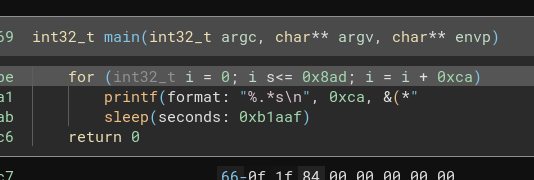
First thing we can see in the main function, its printing something and then sleeps for god knows how long XD
it’s pretty straightforward, we just patch and rmeove that sleep command, then save it and run the file.
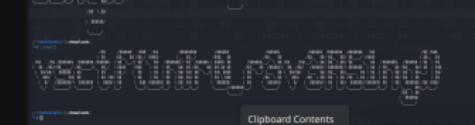
Flag: vsctf{1nTr0_r3v3rR51ng!}
awa-jelly
JellyCTF has some amazing challenges on Jelly Hoshiumi (星海ジェリー), one of the few VTubers who loves CTF. Inspired by a challenge, I made one based on AWA5.0. Can you find the redacted input that matches the screenshot?
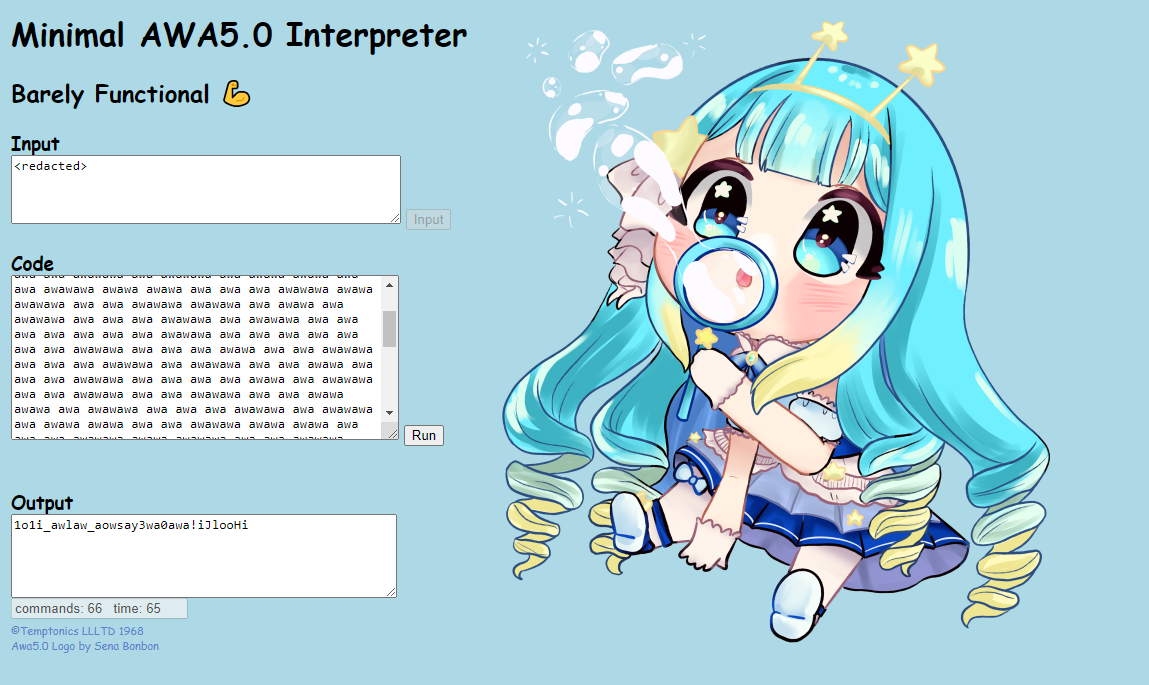
File: awawa.txt
Looking at the image, I immediately started experimenting with the output and given txt file.
First I wasn’t able to understand much on how the awa code works, so i read through the given github link.

Well i found that the language uses infinite FILO stack that holds bubbles, So the intructions need to passed in reverse order. The characters k,q,v,x,z are obsolete which was actually useful to know. I tried to work around with this by running a test string as input to see what output we get. Running a few iterations,
I noticed it just transposes text and is easy to just map out.
py
Now reversing this and applying it on output string
py
And there you have it!
Flag: vsctf{J3lly_0oooosHii11i_awawawawaawa!}
